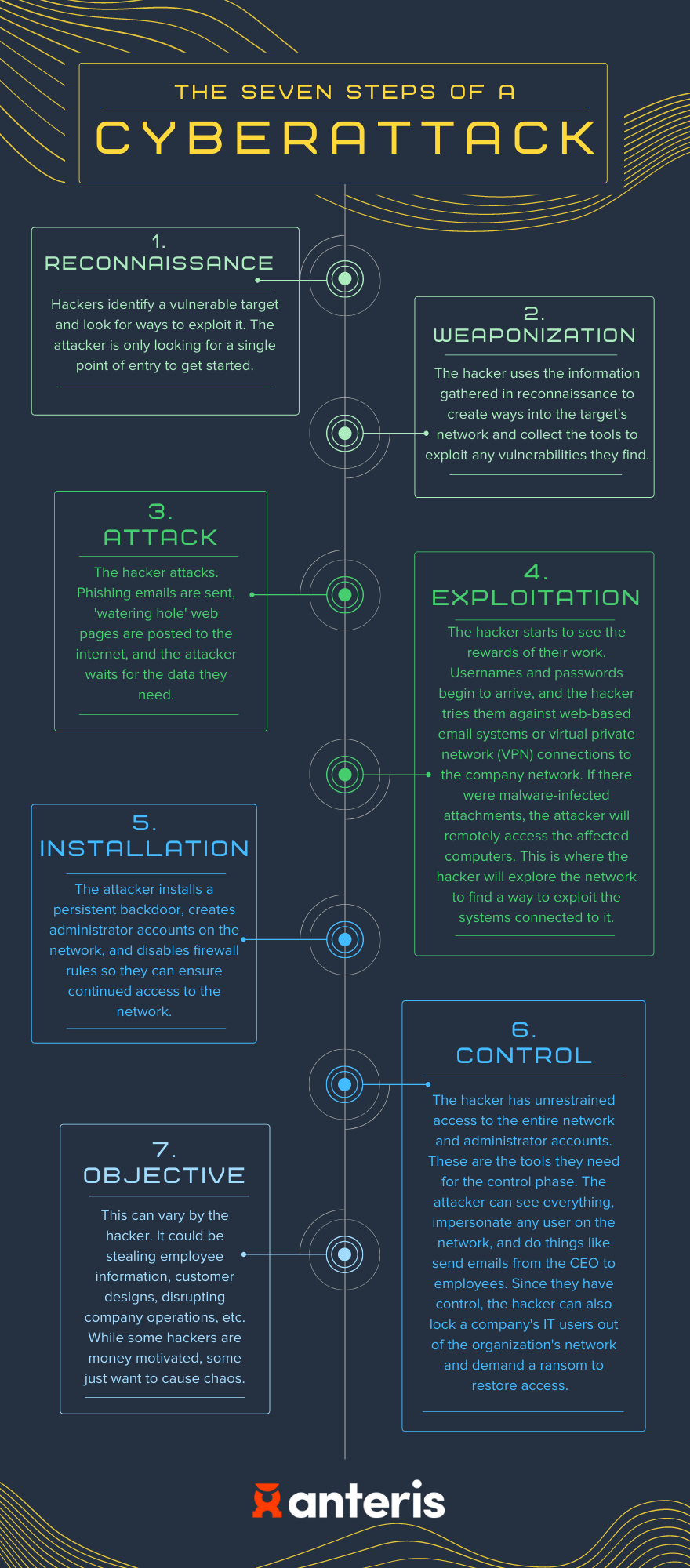
Cyber threats are something that most business owners have on their minds. These security threats can take many forms, but regardless of what form they take, it is imperative to know who to spot them. In general, there are seven steps taken by a cyber attacker.
What this means for you
It is important to understand the seven steps of a cyberattack so that you, and your employees, can recognize the signs. A cyberattack can bring your operations to a screeching halt and compromise your business reputation.
How Anteris can help
At Anteris, we believe in prevention. We do this in two ways. First, our security services support your business and protect your data from outside threats. This includes services like PII Protect and Active Dark Web monitoring and scanning. Second, we believe that education and training are just as important as monitoring in preventing attacks. We provide education and training to make employees aware of the security dangers and provide them with the knowledge of the best practices for protecting against cyber threats. Schedule an appointment with us to find out how we make technology freeing (and safe), not frustrating.




